Similar Tracks
Breaking Through Another Side: Bypassing Firmware Security Boundaries from Embedded Controller
Black Hat
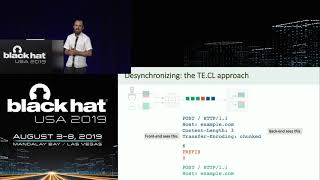
albinowax - HTTP Desync Attacks: Smashing into the Cell Next Door - DEF CON 27 Conference
DEFCONConference
JavaScript Tutorial For Beginners | JavaScript Training | JavaScript Course | Intellipaat
Intellipaat
Data Analytics for Beginners | Data Analytics Training | Data Analytics Course | Intellipaat
Intellipaat