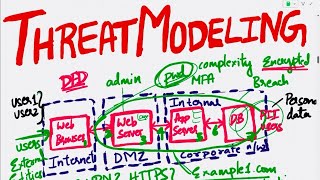
Threat Modeling Explained| How to implement threat modeling| Pros and Cons of Threat Modeling Method
Similar Tracks
Symmetric vs Asymmetric Encryption| Comparison between Symmetric & Asymmetric Cryptograph| Encrypt
CyberPlatter
Explain Access Control Types| Administrative, Logical, Physical| Preventive, Detective, Compensating
CyberPlatter
The Complete Qualys Vulnerability Management Training #cybersecurity #vulnerability
Cyber Technical knowledge
What is Defense-in-Depth? | How to implement defense-in-depth| Layered Security| Cybersecurity
CyberPlatter