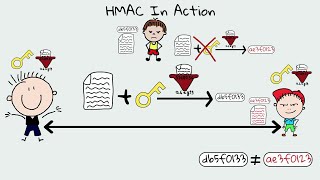
HMAC & Message Authentication Codes (MACs) - Why Hashing alone is NOT ENOUGH for data integrity
Similar Tracks
Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - Cryptography
Practical Networking
Cybersecurity Architecture: Fundamentals of Confidentiality, Integrity, and Availability
IBM Technology
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
First American Pope Makes History and MAGA Catholics Already Have Issues | The Daily Show
The Daily Show
Lagu Malaysia Menyentuh Hati | Lagu2 90an Sungguh Merdu | Lagu Jiwang Malaysia 80-90an Terpopuler
Vinyl Records
Public and Private Keys - Signatures & Key Exchanges - Cryptography - Practical TLS
Practical Networking