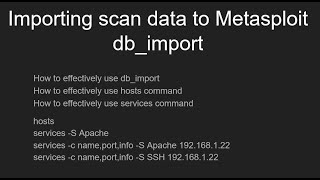
Effectively use database import with Metasploit: Commands - hosts, services | importing scan results
Similar Tracks
Passive information gathering using Metasploit auxiliary module: hands on tutorial using Kali Linux
Cloud Security Training & Consulting
how the OSI model works on YouTube (Application and Transport Layers) // FREE CCNA // EP 5
NetworkChuck
Nmap TCP (sT /sS), UDP (sU), OS detection (O), Version Detection (sV) + Wireshark Analysis
Cloud Security Training & Consulting
Demo: Eternal Blue Exploit using Kali 2022 and Metasploitable3 Windows Server 2008 Hands on guide
Cloud Security Training & Consulting
Arp_Sweep : Host Discovery with Metasploit & Wireshark packet analysis: Auxiliary module - Hands On
Cloud Security Training & Consulting
8 Most Common Cybersecurity Threats | Types of Cyber Attacks | Cybersecurity for Beginners | Edureka
edureka!